Learn what a reverse proxy is and how it can optimize server speeds and help keep your website safe using a firewall.
A reverse proxy is a server that sits in front of another server, acting as an intermediary. The reverse proxy acts as a “middle man” between the client and the actual application. It can also improve the performance and security of network connections by forwarding requests from one server to another.
In this article, find out what uses reverse proxies have and how they’re different from other proxies.
The difference between a reverse and forward proxy.
A reverse proxy is a proxy server that forwards all requests to another server. Meanwhile, a forward proxy acts as an intermediary between two servers.
Proxy server vs. reverse proxy.
There are two main types of proxy servers that you can use: a reverse proxy and a forward proxy.
A reverse proxy acts as an intermediary between the client and the Internet. It enables you to access your website outside without opening port 80 on your firewall or router. This is because it allows you to use any IP address to access your site, making it easier for users who are not in front of their own computers.
A forward proxy server works differently than a reverse proxy server. Instead of acting as an intermediary, it requests directly to another computer on the network. The advantage of this approach is that if someone tries accessing one of these sites through its IP address, they can see all other websites hosted under that exact domain name.
What are the uses for a reverse proxy?
There are many uses for a reverse proxy, although they’re not as valuable as residential proxies. We’ll look at how reverse proxies can offer load balancing to optimize website processing, enhance security, serve static and dynamic content, improve SEO, and communicate between networks.
Optimize for speed with load balancing.
Reverse proxy load balancing is a method of distributing traffic across multiple servers. This method’s primary purpose is to improve your web application’s performance and availability by distributing incoming client requests to various servers. In addition, you can also use it for load balancing purposes.
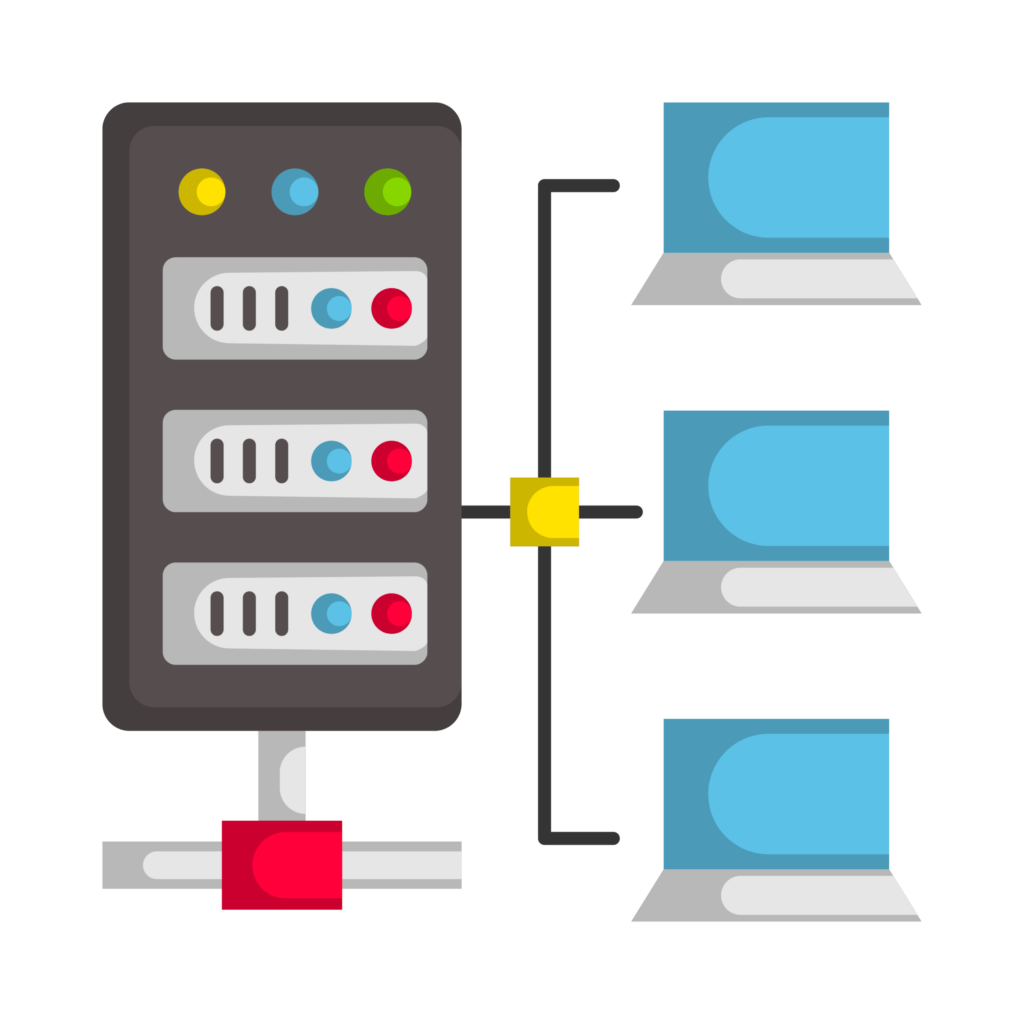
The reverse proxy load balancer uses a list of virtual IP addresses configured on each server cluster. When HTTP requests arrive at the client, they pass to one or more backend servers. These backend servers will then process the requests and responses sent back to clients as needed.
How does Reverse Proxy Load Balancing Work?
This process continues until all backend servers have handled all requests or until no more connections are waiting for processing on any given server in the cluster (a timeout). Once all requests are complete, they are sent back out again. This time with a response code indicating success or failure, depending on whether they were handled successfully.
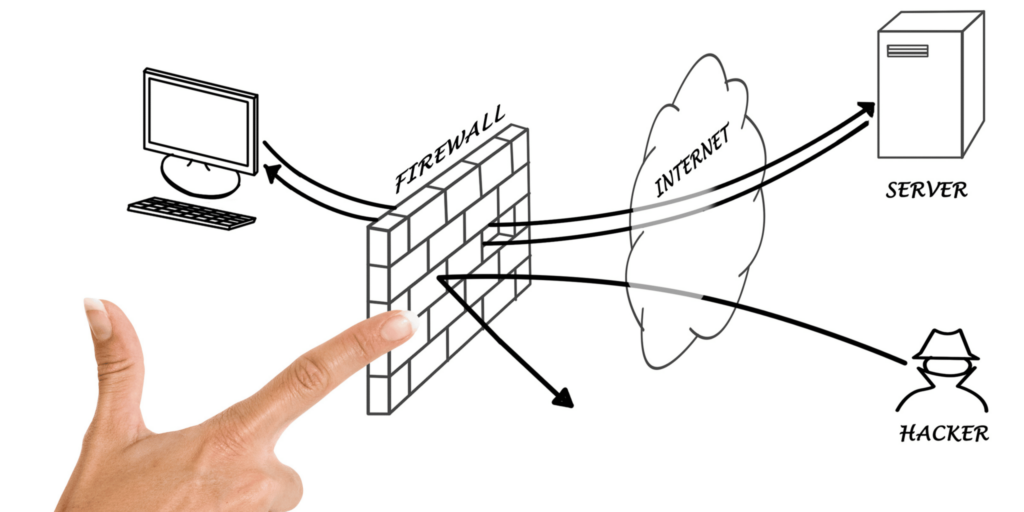
Enhance security with encryption and firewalls.
The main idea behind reverse proxies is to provide security and performance benefits to web applications. It does this by allowing them access only from certain locations or networks or through specific ports (for example, 8080). As such, they are sometimes called “reverse-proxy firewalls.”
The reverse proxy sits in front of your existing web servers and provides additional security. Simply put, it hides the internal structure of your internal network. It also enables you to add SSL encryption for all your traffic. That way, all data is encrypted before being sent out over the Internet from your infrastructure.
A rotating residential proxy can add another layer of security by increasing anonymity by frequently changing IP addresses. It allows you to hide your identity while sending unlimited requests to web servers.
What is SSL?
SSL stands for Secure Sockets Layer, a protocol used to encrypt information sent over a computer network. It uses public-key cryptography to secure data transferred between two computers or networks. In addition, SSL provides authentication so users can be sure they’re connecting with whom they think they are. For example, when you open Google Chrome, you may notice that there is a lock icon in the address bar. This indicates that your connection has been secured using SSL encryption technology.
SSL Termination is a cost-effective way to secure your web applications and services. It provides the same level of security that you get with expensive certificates, but without the hassle and expense. SSL Termination is an ideal solution for hosting providers who want to offer customers a more secure experience while lowering costs. They do this by eliminating the need to purchase additional certificates or install them on their own servers.
Serve static and dynamic content from your backend servers.
You could use one machine for static content and another for dynamic content; both would have their own virtual IP address but share the same hostname.
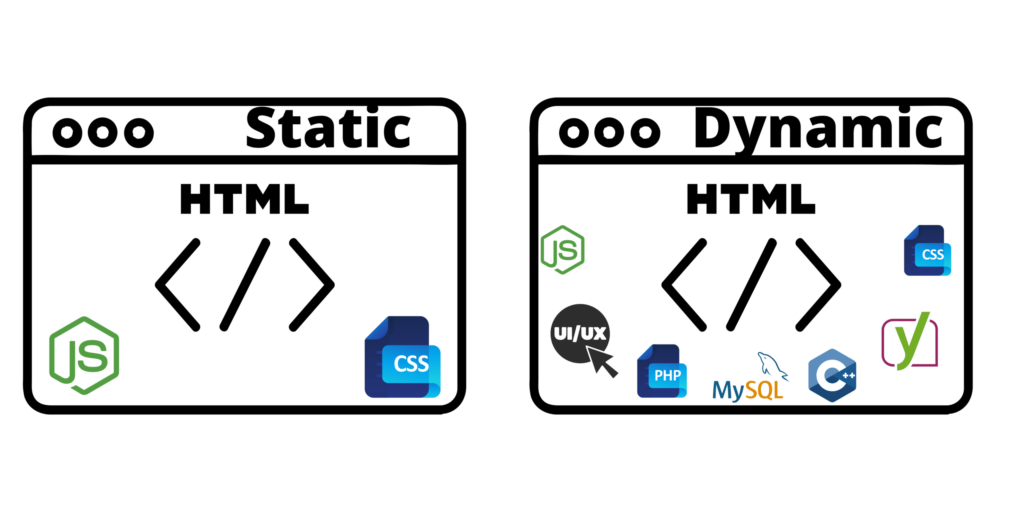
However, there are some drawbacks to using this approach.
- It requires more hardware than just two machines sharing one IP address.
- Each device has its own software installed, which must configure separately.
- If you want different services on each machine, then you will need separate configuration files for each service.
Another issue with using separate hosts is that when you restart the machines, they no longer talk to each other unless you update their configuration. This is not a problem if you use the same hostname for all your servers, but it can be a pain when you have multiple hosts with different names and IP addresses. In this case, you will need to update each machine’s configuration files separately.
URL rewriting to improve your SEO.
URL Rewriting or Domain Mapping is the process of changing or modifying a URL to make it more meaningful for visitors and search engines. You can do this by adding new parameters, removing some parameters, or even creating new URLs from scratch.
The main goal of URL Rewriting is to improve the user experience and SEO performance. It does this by adding new parameters or removing unwanted parameters. It also ensures that links on other websites point back to the same page as yours. For example, you may have an affiliate program linking out to another site. Domain mapping creates new URLs from scratch (also known as 301 redirects).
Providing access between networks.
Reverse proxies are also helpful when there is no direct access between two networks or locations. For example, you may have one network that only has access to the Internet and another network that only has access to internal resources such as databases and file servers.
In this case, you could use a reverse proxy on the Internet-facing side. As a result, any requests from the internal network would go through it before being forwarded onto the public Internet. If your application needs to make requests directly over HTTP, you would still send these requests on their separate path; they would go through an extra software layer before reaching their destination.
The idea behind this approach is that there should be no way for an attacker on either side of your setup to gain direct access via HTTP. That is unless they somehow manage to get past both layers of security (the reverse proxy firewall and web server).
Another situation where reverse proxies can come in handy is if you want one set of applications running in production. In contrast, another group runs in development mode under a different or subdomain name without having them interact with each other.
Proxies can also be used for data mining, like when web scraping.
FAQs.
What is the difference between a reverse proxy and a load balancer?
A reverse proxy server acts as an intermediary between the client and the original web application. A load balancer is an intermediary between multiple web applications (or services). Sometimes, they may also act as a caching layer for content served from another server.
Is a reverse proxy safe?
Reverse proxies add to the safety of your web operations by adding a layer of encryption and anonymity. There is the possibility of proxies creating security vulnerabilities if you aren’t the proxy administrator. In this case, you won’t know what information is being monitored.


