In today’s world, where everything is connected via the internet, understanding IP networks and subnetting is crucial. But what are subnet masks? Why are they important in network division? And how do they work with IP addresses?
In this beginner’s guide to IP networks and subnetting, we will cover all these topics and more. We will also provide you with tips and tricks for subnetting that you can use in your daily life. Additionally, we will discuss how subnets are relevant for proxy servers, including IP blocking and subnet bans. Lastly, we will introduce you to IPBurger’s residential proxies – a tool that can help you take your online security to the next level.
Let’s dive in!
What’s a Subnet Mask?
A subnet mask is a crucial component of IP networks that helps divide a larger network into smaller subnetworks or subnets. It is a 32-bit number that works in conjunction with an IP address to determine the network and host portions of an IP address. Four octets separated by periods represent the subnet mask, with each octet representing eight bits.
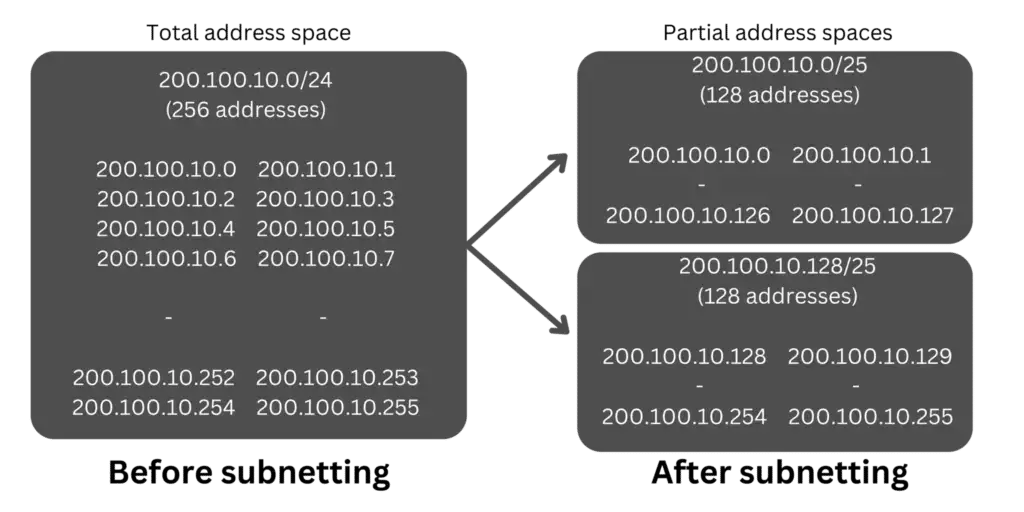
The first octet of the subnet mask is typically 255, indicating that an IP address with a matching octet belongs to the single network portion of the address. The last octet of the subnet mask is typically 0, indicating that an IP address with a matching octet belongs to the host portion of the address.
Vocabulary
Network ID: The network ID is a portion of the IP address that identifies a specific network prefix. In conjunction with the IP address, the subnet mask determines it.
Data Packet: A data packet is a data unit transmitted over a network number. It contains the necessary information to deliver the data from one device to another, including the source and destination IP addresses and any data payload.
Gateway: A gateway is a networking device that connects two different networks. It acts as the entry and exit point for traffic between the networks, allowing devices on one network to communicate with devices on another network.
Router: A router is a networking device that forwards data packets between computer networks. It determines the best path for the data and ensures it reaches its destination.
Internet Protocol: The Internet Protocol (IP) is a set of rules that govern how data is transmitted over the Internet. It provides a unique address for each device connected to the internet so that data can be sent and received between them.
TCP: The Transmission Control Protocol (TCP) is a protocol that allows for reliable and ordered delivery of data between devices over a network. It works in conjunction with IP to form the basis of Internet communication.
Host ID: The host ID refers to the portion of an IP address that identifies a specific device on a network. The subnet mask determines it and helps to direct data packets to the correct destination.
RFC: The Request for Comments (RFC) is a series of memos that outline various technical aspects of Internet communication, including the standards and protocols used.
DHCP: The Dynamic Host Configuration Protocol (DHCP) is a protocol that automatically assigns IP addresses to devices on a network.
IPv4 vs IPv6
Before we delve deeper into subnet masks, it’s important to understand the difference between IPv4 and IPv6.
IPv4 is a 32-bit address format that can support up to 4.3 billion unique IP addresses. However, with the exponential growth of devices connected to the internet, these addresses are becoming scarce.
This is where IPv6 comes in with its 128-bit address format, providing an almost infinite number of unique addresses for every device on the internet. Despite this, many networks still rely on IPv4 and require subnet masks to manage their network traffic effectively.
Importance of Subnet Masks in Network Division
Proper network division is essential for improving the performance and security of IP networks. Subnet masks play a vital role in this process by dividing a larger network into smaller subnetworks or subnets. The subnet mask identifies the network portion and host portion of an IP address, allowing for better control over network traffic and access.
Administrators can create separate subnets for different organizational departments or groups by using subnet masks, improving overall network efficiency. A well-designed subnetting scheme can also help reduce network congestion and prevent unauthorized access to sensitive information. Therefore, understanding how subnet masks work and choosing the right one based on your network size is essential for effectively managing and troubleshooting IP networks.
Classes of Subnets
Now that we understand the importance of subnet masks let’s dive into the different classes of subnets: Class A, Class B, Class C, Class E, and Class D.
- Class A subnets have a default subnet mask of 255.0.0.0 and can support up to 126 networks with—an IP range of 16,777,214 hosts per network.
- Class B network subnets have a default subnet mask of 255.255.0.0 and can support up to 16,384 networks with 65,534 hosts per network.
- Class C network subnets have a default subnet mask of 255.255.255.0 and can support up to 2,097,152 networks with 254 hosts per network.
- Class E is reserved for future use, while Class D is used for multicast addresses.
Understanding IP Address and Subnet Mask
When it comes to networking, an IP address is a unique identifier assigned to each device on a network. It allows devices to communicate with each other and access resources on the network.
However, a network address alone does not provide enough information to determine network boundaries or the number of available hosts. This is where subnet masks come in.
A subnet mask determines the network portion and host portion of an IP address, allowing for better organization and management of IP addresses. You can divide a large network into smaller subnetworks by subnetting, improving efficiency and security. Understanding how IP addresses and subnet masks work together is crucial for any IT professional or network administrator.
Benefits of Using Subnet Masks
Subnet masks are a crucial component of IP networks and have several benefits.
- They help divide a network into smaller, manageable subnetworks. This enables better management and organization of devices on the network.
- Subnets reduce network congestion and improve network performance by limiting broadcast traffic within each subnet.
- They allow for more efficient use of IP addresses. By assigning specific IP addresses to each subnet, administrators can ensure each device has a unique destination address while minimizing the wastage of IP addresses.
- Subnetting enhances network security by isolating different groups of computers and devices, making monitoring and managing access to resources easier. Overall, using subnet masks is essential for effectively managing large networks.
How Are Subnets Relevant for Proxy Servers?
Proper subnetting plays a crucial role in configuring proxy servers. A subnet mask determines the range of IP addresses available for use in a network segment, limiting access to specific IP addresses and improving network security.
Along with enhanced security, subnetting can also help reduce network congestion and improve overall network performance. Using subnets to divide larger networks into smaller, more manageable ones makes assigning specific IP addresses to particular devices easier, allowing for more efficient use of available resources.
Proxy server configurations can benefit greatly from proper subnetting practices, making it an essential element of any network management strategy.
IP Blocking
IP blocking is a crucial aspect of proxy server configuration, which uses subnets to block entire ranges of IP network addresses. This practice is commonly used to restrict access to specific websites or online content.
By using subnet masks, proxy servers can efficiently manage and control access to different IP addresses. In other words, subnetting allows for creating multiple subnetworks within a larger network, each with its own range of IP addresses. By doing so, proxy servers can effectively block or grant access to specific IP addresses in an even more precise manner.
Overall, subnet masks play a vital role in enhancing the security and performance of networks while improving the efficiency of proxy server configurations.
Subnet Bans
Subnet bans are standard practice websites and servers use to prevent malicious activities like hacking attempts and spamming.
When a user’s IP address falls within a banned subnet range, they may be unable to access the website or server. However, proxy servers can bypass these subnet bans by changing the visible destination IP address.
Remembering that using proxies responsibly is of utmost importance, and they should not be used for prohibited activities. By taking these precautions, users can effectively bypass subnet bans and access restricted content without risking legal consequences.
Tips and Tricks for Subnetting
When it comes to subnetting, several tips and tricks can help simplify the process.
1. Buy Proxy IPs from Multiple Subnets
When buying proxy IPs, ensuring they are from multiple subnets is essential. This approach provides several benefits, including improved security and reliability for your network. By purchasing proxy IPs from different subnets, you can distribute your traffic across various IP ranges, which helps prevent IP blocking or blacklisting. Additionally, having access to multiple subnets gives you greater flexibility in managing your network traffic and customizing your routing rules.
However, choosing reputable providers that meet your specific subnetting needs is crucial when selecting proxy IPs from multiple subnets. Doing so will help ensure you have the right tools to keep your network secure and operating smoothly. So if you want to optimize your proxy server performance while maintaining security, be sure to consider purchasing proxy IPs from multiple subnets.
2. Get a Private Subnet for Yourself
Maintaining network privacy and security is crucial for individuals and businesses. Creating a private subnet for your devices can safeguard against potential threats while giving you more control over your network traffic. A private subnet allows you to connect various devices to a network without exposing them to the public internet. This way, you can mitigate the risk of unauthorized access and protect sensitive information from prying eyes.
Choosing an IP host address range not commonly used on public networks will prevent conflicts and ensure seamless connectivity across all your devices. Subnetting can be used in small or large networks, allowing for better device organization and management. It’s important to note that creating a private subnet does not make your network completely invulnerable to attacks. Still, it vastly reduces the risk of breaches by adding an extra layer of protection between your devices and external threats.
3. Use Residential Proxies
When it comes to online privacy and security, using residential proxies can be a game-changer. Residential proxies are IP addresses that Internet Service Providers (ISPs) assign to homeowners, making them less likely to raise a suspicious flag. This means you can access restricted networks and hide your original IP address without detection. Additionally, residential proxies can help you bypass geo-restrictions and access content that is not available in your region.
However, not all residential proxies are created equal. Choosing a reputable provider with reliable performance and security features is important. Some popular options include Luminati, Smartproxy, and Oxylabs. These providers offer high-quality residential proxies with features such as rotating IPs, automatic session management, and 24/7 support. Using residential proxies from a trusted provider, you can protect your online identity and access the internet with greater freedom and flexibility.
IPBurger’s Residential Proxies
Regarding online security and privacy, using a proxy server effectively protects you from prying eyes. However, not all proxies are created equal.
Residential proxies, like those that IPBurger offers, have a number of advantages over other types of proxies. One of the key benefits of residential proxies is the fact that they use IP addresses assigned by Internet Service Providers (ISPs) to homeowners. This makes them less likely to be flagged as suspicious and more difficult for websites or services to detect.
In addition, using residential proxies can provide access to restricted networks or content that may be blocked in certain regions or countries. By masking your true location with the IP address of a residential proxy, you can bypass these restrictions and access content that would otherwise be unavailable. Overall, residential proxies provide a reliable and secure way to protect your online activity and gain access to restricted content.
Conclusion
Subnet masks play a crucial role in network division and IP addressing. They are used to divide IP address ranges into smaller subnets, allowing for more efficient use of IP addresses and better management of network traffic. Understanding subnetting can be overwhelming, but you can easily navigate through it with the right knowledge and tools.
Here at IPBurger, we offer residential proxies that come from various subnets across multiple locations worldwide. This means you get access to a diverse pool of IPs that can help you bypass restrictions and access geo-restricted content across the web.
So why wait? Try our residential proxies today and take your online experience to the next level!



