WebRTC as a privacy risk
The protocols implemented by WebRTC such as STUN make the Public IP address of a user discoverable. This is a privacy risk if malicious actors can utilize the STUN protocol and get your public IP address from your browser. Other agencies can even track and monitor your activities over the internet.
Checking for WebRTC Leaks
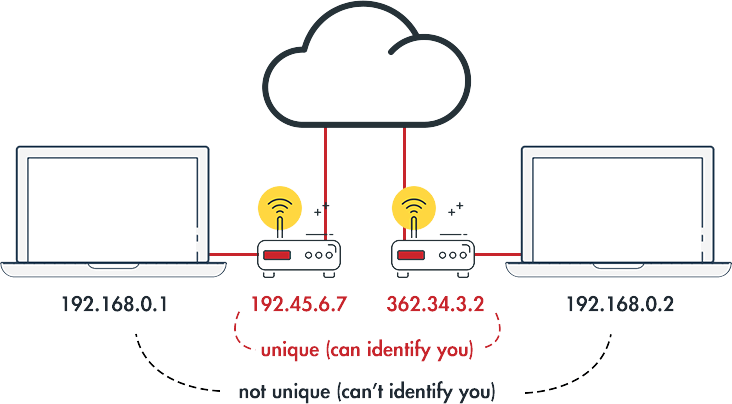
At times when using WebRTC, public IP leaks may occur or may not. If you are not sure if there’s a leak, the simplest way to confirm your doubts is by performing a WebRTC leak test. When performing this test, the results usually contain two IP addresses, your local IP address, and your Public IP address. Local IP addresses are not that unique because they are assigned to you by your router. Chances are, everyone who has a router will have the same local IP address as you. This IP is not much of a threat if you see it in the tests.
Your Public IP address, however, is what you should pay attention to. Its unique to you and it’s the one used to identify you on the internet.
Performing the WebRTC Leak test
A WebRTC leak test is used to show if your browser is leaking. More importantly, it indicates if your VPN can protect you against this browser WebRTC leaks.
When using a VPN, your Public IP address is hidden and what is visible is the VPN’s IP address. If a WebRTC leak occurs, the VPN is supposed to ensure your Public IP address is protected. But if that’s not the case, your unique Public IP address will be visible and that’s a privacy risk from a VPN that’s is supposed to protect you.
To determine if your VPN is leaking or you have a WebRTC leak, use the following procedure;
Launch your browser and open a WebRTC Leak Test page
Note the Public IP address that will be shown.
After that, close the page and the browser
Now connect to your VPN and reopen the browser and the page
If you still see the public IP address that you noted, then you have a privacy leak, and your VPN isn’t doing any job in protecting the leak. If you see your VPN’s server IP address, then you are safe.
Preventing WebRTC Leaks
WebRTC leaks are common in browsers, but usual culprits are Mozilla Firefox and Chrome. These browsers are vulnerable because WebRTC is enabled by default. They are also the most used browsers in the world. The Apple browser, Safari, isn’t much affected by WebRTC leaks. To prevent WebRTC use the following ways;
Use IPBurger VPN
Most VPNs overlook the WebRTC threat, and hence they don’t offer protection against its leaks. IPBurger VPN is different right from the way it's engineered. IPBurger VPN protects your online identity by ensuring leaks such as WebRTC, IP and DNS leaks don’t occur.
Disabling WebRTC in browsers
Besides using a VPN, you can take an extra precautionary measure to ensure WebRTC isn’t enabled by default in your browser. Well look at how to disable WebRTC in Mozilla Firefox and Chrome
How to disable WebRTC in Firefox
- In the URL bar/Address bar, type about:config
- Click “I accept the risk!” on the page that opens
- Next, type media.peerconnection.enabled in the search bar
- Double-click on the entry that comes up to change the Boolean value from true to “false”
How to disable WebRTC in Chrome on desktop
In Chrome and Chromium browsers, there are no technical steps involved. All you need to do is download an official Chrome extension known as WebRTC Network Limiter. This extension prevents IP leaks without entirely disabling WebRTC.

100% Satisfaction Guarantee
We’re absolutely sure that IPBurger provides the highest quality IPs with the strictest privacy protections and fastest connections available that if you're not satisfied we will replace or provide credit for any service purchased for the term of your subscription.
 Chrome
Chrome Firefox
Firefox